SSH IPv4 to IPv6 using TOR

In previous article, we discussed the challenges for SSH connection between IPv4 and IPv6. This is a tutorial post on how to SSH from IPv4 network to IPv6 network using TOR.
What is TOR
The TOR (The Onion Router) network is a free, open-source network of servers that can be used to anonymize Internet traffic. It is designed to protect the privacy and security of Internet users by routing traffic through multiple servers, or "nodes," before it reaches its destination. This makes it difficult for anyone to track the origin or destination of the traffic.
TOR is often used by individuals who want to protect their privacy online, such as journalists, activists, and whistle-blowers. It is also used by companies and organizations to protect their network and data from cyber threats.
It is not specifically designed to connect IPv4 to IPv6, but rather to provide anonymity and privacy for Internet users. That being said, the Tor network does support both IPv4 and IPv6, and it is possible to use the Tor network to connect an IPv4 device to an IPv6 resource, or vice versa. This can be done by using a Tor relay that supports both IPv4 and IPv6.
For example, an IPv4 device can connect to the Tor network using an IPv4-only connection, and then exit the network through an IPv6-enabled relay to access an IPv6 resource. Alternatively, an IPv6 device can connect to the Tor network using an IPv6-only connection and exit the network through an IPv4-enabled relay to access an IPv4 resource.
Step 1: Download and install TOR
- Head over to this link: https://www.torproject.org/download/ and download TOR for your operating system
- For Windows and Mac you will get an executable file which will work by double-clicking; for Linux it's you need to follow the installation instruction guide available here. - https://tb-manual.torproject.org/installation/
Step 2: Running TOR
Basically, TOR is a browser and will look and feel like Firefox. Just open TOR and press the Connect button on startup page
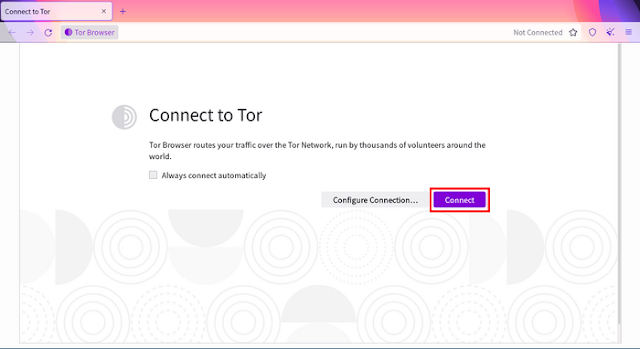
If you face any problems in connection, head over to this link https://tb-manual.torproject.org/running-tor-browser/ for troubleshooting
Step 3: Using TOR's SOCKS proxy
The TOR network includes a SOCKS proxy that allows users to route their traffic through the TOR network. When a user connects to the TOR network using the SOCKS proxy, their traffic is encrypted and sent through multiple TOR nodes before it reaches its destination. This makes it difficult for anyone to track the origin or destination of the traffic.
To use the TOR SOCKS proxy (version 5), you will need to configure your application to use the SOCKS proxy and specify the address and port of the TOR SOCKS proxy. The default address and port for the TOR SOCKS proxy is "localhost" and "9150," respectively.
In our case, we want to use the SOCKS 5 on our Command prompt or Terminal window for the SSH connection.
For Windows
First install nmap from this link. nmap package includes the ncat we are going to use for connection.
After setup is finished, you can check if ncat is properly installed using this command
ncat --version
Then, to make the SSH connection, use the below command. Note that TOR is slow, and the connection initiation may fail some time, so you need to try a few times
ssh -o "ProxyCommand ncat --proxy-type socks5 --proxy 127.0.0.1:9150 %h %p" user@hostname
The ssh command is used to establish an SSH connection to a remote host. The -o option is used to specify options that are applied to the entire command.
The ProxyCommand option is used to specify a command that should be run to establish the connection to the remote host. In this case, the command ncat --proxy-type socks5 --proxy 127.0.0.1:9150 %h %p is used to connect to the remote host through a SOCKS 5 proxy running on the local machine at 127.0.0.1 on port 9150 (this is the configuration for TOR Network). The %h and %p variables are replaced with the hostname and port of the remote host, respectively.
The ncat command is a networking utility that can be used to read and write data across a network connection. It is similar to the nc (netcat) utility. The --proxy-type option is used to specify the type of proxy to use, and the --proxy option is used to specify the hostname and port of the proxy server (127.0.0.1:9150).
For Mac OS / Linux
Use below command for connection
ssh -o ProxyCommand='nc -X 5 -x 127.0.0.1:9150 %h %p' user@hostname
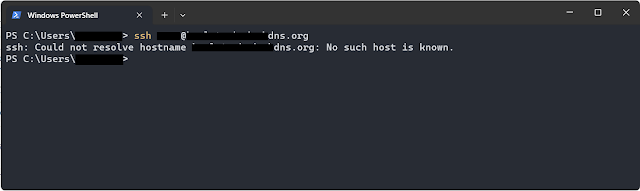
You should be able to successful able to connect (SSH) from IPv4 only network to IPv6 network. IPv4 unable to connect to IPv6 network without TOR proxy
IPv4 connected to IPv6 network using TOR proxy
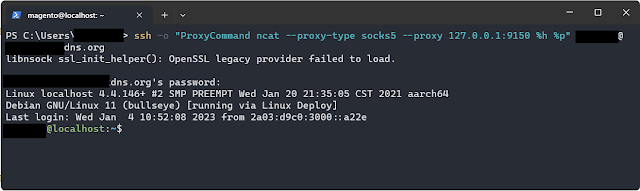
The downside to this method is connection speed, as TOR network is slow due to multiple routing and extra security.
In the next article, we will talk about using a Tunnel Broker for SSH connection between IPv4 and IPv6.
Till then stay safe, wear mask and Save Soil.